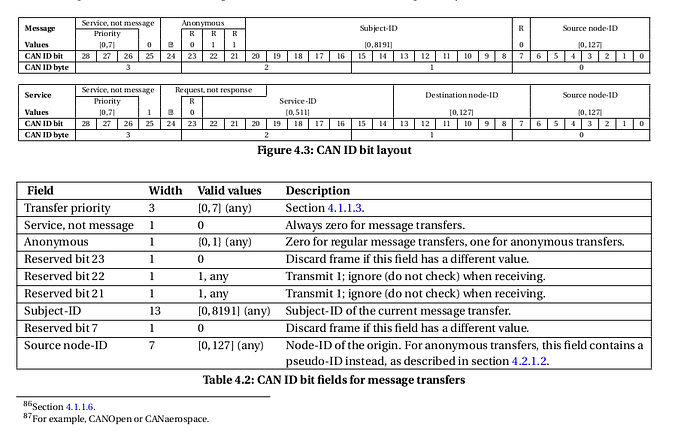
Here is another idea. We have several reserved bits in the current v1 beta spec that are reserved. Here is the current packet format:
Bit 23 is marked as discard if bit isn’t 1. We could change that to be that when bit 23 is 0 the subject ID is used as a semantic ID.
Then we’d have DSDL like this:
# GNSS message
@semantic_id 17
uint3 instance
uint3 status
uint32 time_week_ms
uint16 time_week
int36 latitude
int36 longitude
float32 altitude
float32 yaw
uint16 hdop
uint16 vdop
uint8 num_sats
float32 velocity[3]
float16 speed_accuracy
float16 horizontal_accuracy
float16 vertical_accuracy
float16 yaw_accuracy
note the @semantic_id marker. This would do several things:
- the code generator would automatically fill in the subject_id with the semantic_id when a semantic_id is specified in a message
- bit 23 would be set to 0 in these messages
- the compiler would check that there is no re-use of the semantic_id values across all of the DSDL being compiled for the project
This still allows for v1 to support all the SOA capabilities that Pavel wants to see, while also supporting robust sensor networks which is what we need for ArduPilot and PX4. By using up one reserved bit we get past this logjam in our discussions.